2023 Speakers

Head of Engineering, Glean

Head of Counter Threat Unit, LEGO Group

Specialist Crime Division: Cybercrime Investigations, Police Scotland

Group Threat Intelligence Analyst, The Weir Group

Technology & Cyber Risk Manager, Tesco Bank

Security Manager, Tesco Bank

CISO, Flo Health

CTO, Tremau

CISO, MongoDB

Chief Executive Officer, NCSC

Application Security Engineer, Flo Health

Cyber Incident Response & Threat Intelligence Manager, Cyber and Fraud Centre – Scotland

Director of IT & Operations, Secarma

Senior Enterprise Systems Engineer, SentinelOne

Information Security Awareness, Education and Communications Lead, DWS Group

Vice President, CTU, Secureworks

Director UK & Ireland Sales, BlackBerry Cybersecurity

Global Head, Cyber Security Practice, Business Transformation Group, TCS

Senior Sales Engineer, Arctic Wolf

Cyber Threat Intelligence, Technical Lead, Lloyds Banking Group

Head of Cyber Security, Tesco Bank

Journalist & Broadcaster, BBC Scotland

Founder, DIGIT
2023 Agenda
Thursday 30 March, Dynamic Earth
08.30 Registration desk and exhibition area opens. Tea, coffee and pastries provided.
SESSION 1 Re-watch on YouTube
The opening session will focus on improving the effectiveness of threat detection and response against a backdrop of increased organisational complexity. We will look at optimising internal process, prioritising high-risk attack paths, and addressing some of the persistent failings associated with behavioural security and culture.
09:15 Welcome and Introduction from the Conference Chair
Mark Stephen, Journalist & Broadcaster, BBC Scotland
09:25 Threat Detection and Response in a Product World
Marko Jung, Principal Engineer & Head of Counter Threat Unit, LEGO Group
09:50 Understanding and Prioritising Attack Paths Amid Growing Organisational Complexity
Elliott Went, Senior Enterprise Systems Engineer, SentinelOne
10:10 Why Are We Still Failing to Address the Human Factor?
Robin Lennon Bylenga, Information Security Awareness, Education and Communications Lead, DWS Group
10:35 Combined Q&A
11:00 Networking & Refreshments
SESSION 2 Re-watch on YouTube
Session 2 will explore a series of key topics in a longer presentation format. The session will be run in a breakout format across four parallel streams, providing delegates the opportunity to attend two options live. The alternative breakouts will be accessible on-demand post-event.
11:35 First Breakout Option
12:10 Transition
12:20 Second Breakout Option
12:50 Lunch and Networking
Breakout options include:
A. Threat Intelligence - Panel Session
Panellists include:
• Mike Smith, Cyber Incident Response & Threat Intelligence Manager, Cyber and Fraud Centre – Scotland
• Nick Leitch, Cyber Threat Intelligence, Technical Lead, Lloyds Banking Group
• Jessica Amery, Group Threat Intelligence Analyst, The Weir Group
• DC Kelly Thorburn, Specialist Crime Division: Cybercrime Investigations, Police Scotland
B. API Security: I will IDOR Myself In
• How attackers could gain control of millions of devices by exploiting simple, yet critical API flaws
• How these flaws allow attackers to control and use devices as an initial foothold in large networks
• Exploring the types of devices affected - from routers and alarms to car chargers
• How the era of “central platform” handling that solves a variety of problems backfired by re-introducing a number of old vulnerabilities
Vangelis Stykas, CTO, Tremau
C. Improving Diversity, Inclusion and Resourcing within the Cybersecurity Industry
• Background context on the diversity picture within the industry
• Key objectives of the CIISec D&I programme
• Overview of the different streams and individual focus areas
• The role of the programme in addressing skills and resourcing challenges
• Next steps: opportunity to feedback and help shape future strategy and implementation
Grant Cairns, Cyber Security Manager, Tesco Bank
Durgesh Gaitonde, Technology & Cyber Risk Manager, Tesco Bank
Rory Alsop, Head of Cyber Security, Tesco Bank
D: Rethink your Cyber Resilience Strategy to address Emerging Threats
• How is Cyber Crime & Attack emerging
• Latest threat vectors in ever evolving landscape
• What readiness should organisations have
Kunal V. Pradhan, Global Head of Cyber Security Practice, Business Transformation Group, TCS
---
12:10 Transition
12:20 Second Breakout Option
Breakout options include:
E. Responding to the Ever Evolving Threat Landscape
• How threat actors’ tactics, techniques, and procedures have changed
• The severity of ransomware and how to defend against it
• First-hand experiences and best practices from cybersecurity experts
Don Smith, Vice President, CTU, Secureworks
F. From XDR to CSR: Using Prevent as a Strategy to Protect your Organisation & the Environment
• How mature AI modelling lessens the environmental burden
• More prepared does not equal more resource
• Extend your defence and your lifecycles
Lee Beard, Director UK & Ireland Sales, BlackBerry Cybersecurity
G: Stem the Tide: Rise Above Alert Fatigue and Improve Your Security Posture with Limited Resources
• How to maximise your security posture within your current resource set up
• Whether it’s possible to manage large exposures with limited resources
• What you can do to better develop your teams and raise cyber-awareness throughout your company
Brian Stewart, Senior Sales Engineer, Arctic Wolf
H: Introduction to Threat Modelling and its Benefits to Business
• What is threat modelling and when it is useful?
• Who can and should threat model?
• Threat modelling tools and techniques
• Threat Modelling as a risk management activity
• Threat Modelling Diagram basics
Jen Williams, Director of IT and Operations, Secarma
12:50 Lunch and Networking
SESSION 3 Re-watch on YouTube
The afternoon session will look at embedding a proactive security mindset across your organisation. We will explore how to engage with developers and engineering teams to establish genuine buy-in; how applications can be built with a security-first approach by leveraging tools like anonymisation, and how we can communicate effectively with the board and positively engage C-level decision makers.
13:40 Bringing the Party to Security
Gwen Diagram, Head of Engineering, Glean
14:05 Improving Privacy & Security Through Anonymisation
Leo Cunningham, CISO, Flo Health
Kajus Sestokas, Application Security Engineer, Flo Health
14:30 Talking to the Board
Lena Smart, CISO, MongoDB
14:55 Combined Q&A
15:25 Closing Remarks
15:30 End of Session
---
15:30 Networking Drinks
16:30 End of Summit
---
Virtual Keynote: On Demand WATCH ON YOUTUBE
An Overview of the 2023 Threat Landscape
Lindy Cameron CB OBE, Chief Executive Officer, NCSC
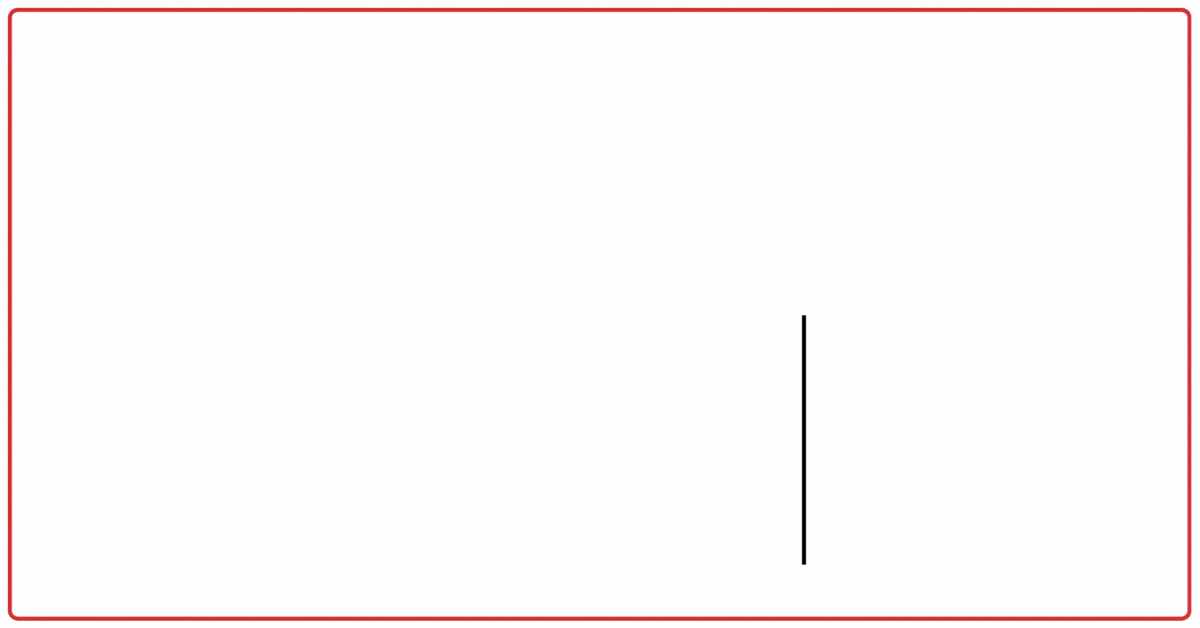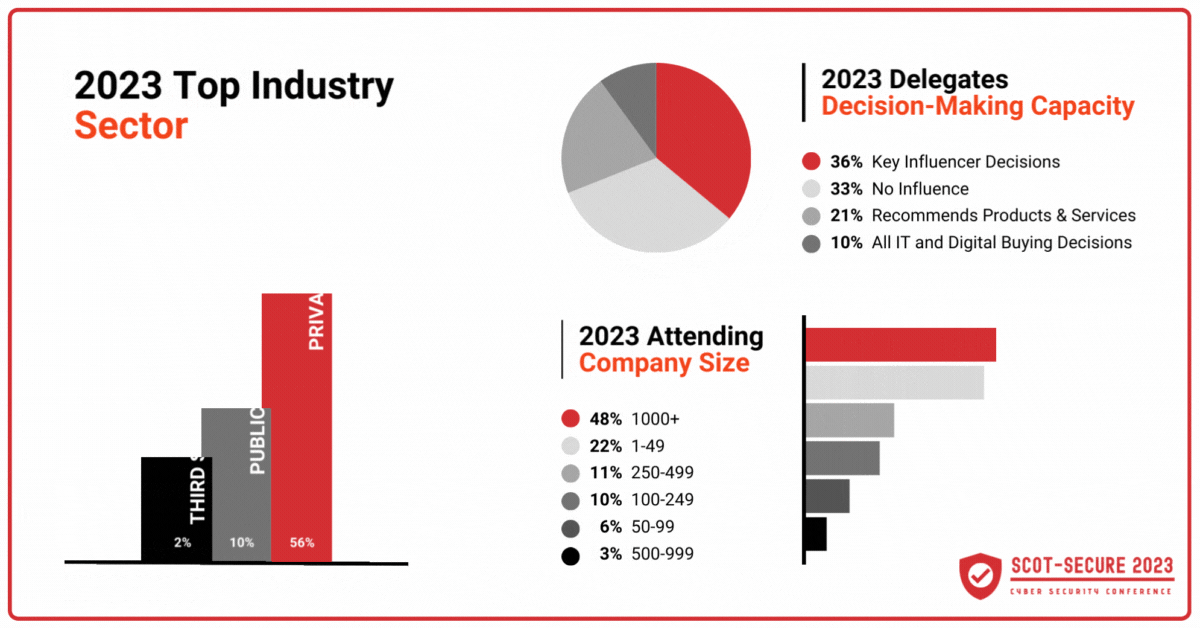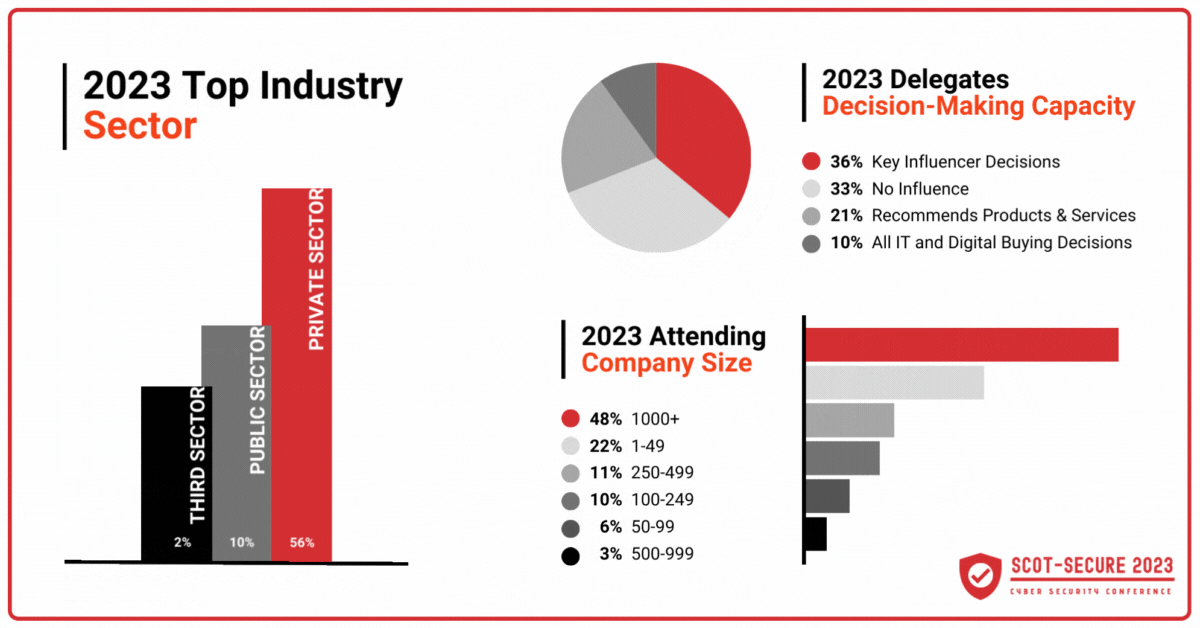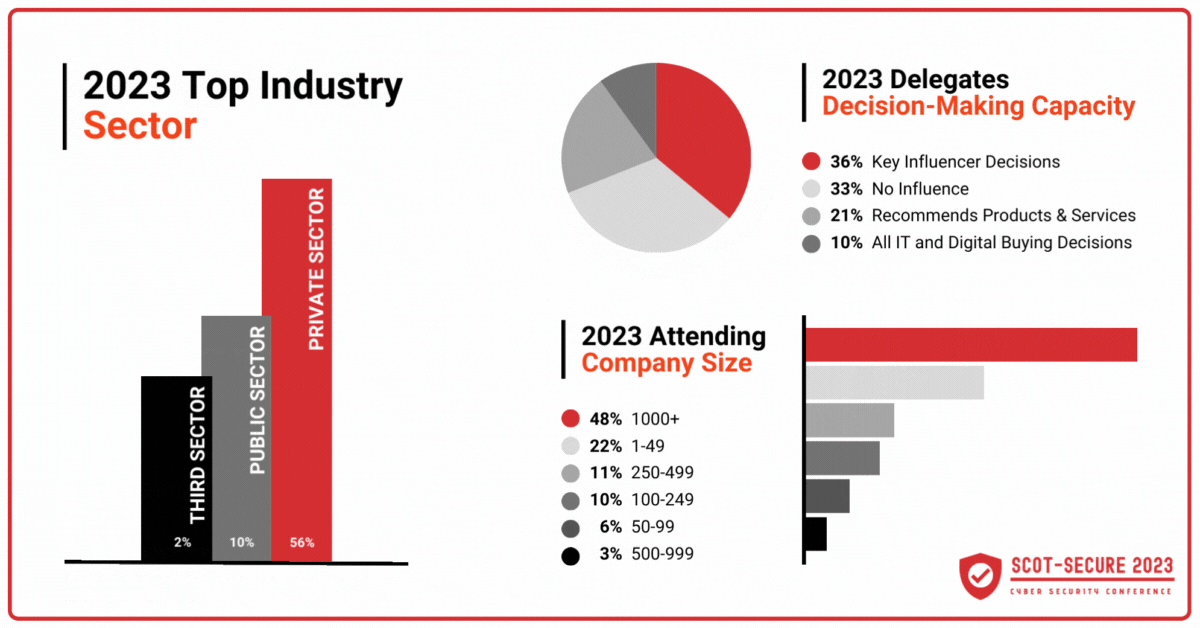
Attendees